CardOS
A high security focused, multi-functional native smart card operating system, providing all functions to cover different applications via contact-based and contactless interface.

NEW!
CardOS Security Token
Smart cards are the foundation of state-of-the-art security solutions based on secure elements, that guarantee identity, control access and enable efficient online private and public interactions with customers and citizens.
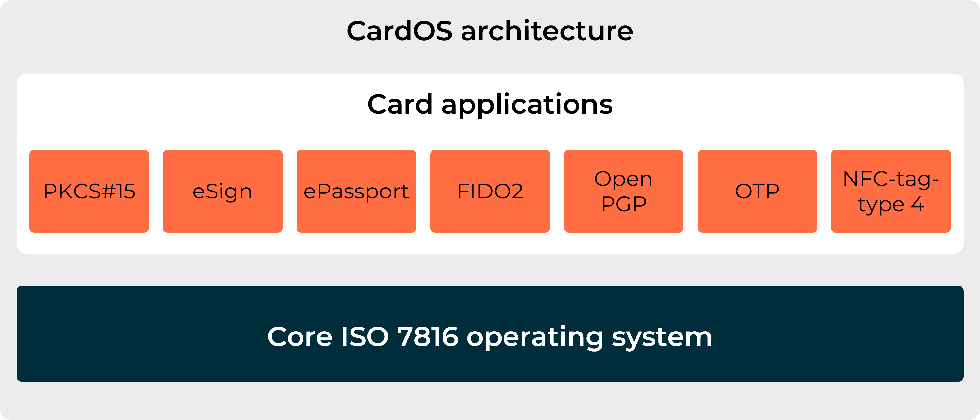
CardOS smart card native operating system provides an outstanding level of functionality and security and offers a multitude of applications like eID, ePassports, citizen cards, health insurance and health professional cards, employee badges, signature cards, as well as loyalty cards.
All applications are expandable by customized packages to amend or adjust the operating system functionalities. Furthermore, the authentication framework is a flexible option to realize authentication protocols by using configuration data.
Additionally, by supporting NFC, CardOS is suited for logical access with mobile devices. Furthermore it offers state-of-the-art crypto algorithms with AES, SHA-2 and elliptic curves.
Certified according to Common Criteria EAL4+, supporting single signature creation, limited and unlimited mass signatures with both RSA and ECC, CardOS is listed as an eIDAS compliant QSCD and QSealCD in the EIDAS member states notification list .
CardOS based smart card solutions enable various use cases across all business processes:
- Central user administration, role administration and single sign-on systems with smart cards
- Document encryption and digital signatures with smart cards (e-mail, documents and media)
- Security solutions with smart card technologies
- Embedded security solutions with smart card controllers
PRODUCT ARCHITECTURE
MODULES, BASICS, KEY FEATURES, COMPARISONS
Contact based
German signature law
Contact based
ECC, Austrian signature law
Dual Interface
Contact based
Contact less
Dual Interface
Contact based
RNG acc. to DRG.4 / PTG.3
Dual Interface
Contact based
for FIDO2 token solutions
Dual Interface
Contact baseds
Contact less
and QSCD/QSealCD eID applications
M: ROM-based implementation
 CLOUD SERVICES
CLOUD SERVICES CITIZEN ID
CITIZEN ID IT SECURITY
IT SECURITY IOT and INDUSTRY
IOT and INDUSTRY PKI SOLUTIONS
PKI SOLUTIONS CREDENTIAL MANAGEMENT
CREDENTIAL MANAGEMENT SECURITY TOKEN & HARDWARE SOLUTIONS
SECURITY TOKEN & HARDWARE SOLUTIONS SECURITY APPLICATIONS
SECURITY APPLICATIONS








