
by Klaus Schmeh | Mar 14, 2025 | Product & Solutions
Cryptovision ePasslet Suite, a Java Card-based framework for implementing eID applications on smart cards, supports a new feature: FIDO2 authentication is now part of the suite.
FIDO2, a global standard for token-based online authentication, ensures simple and secure login without a password and without a public key infrastructure (PKI). With the new function, ePasslet Suite thus offers an additional option for customers who want to do without digital certificates for authentication.
The FIDO2 functionality of ePasslet Suite has been certified by the FIDO Alliance, which underlines the high security and reliability of this feature.
Take advantage of FIDO2 authentication now and protect your digital identities even more effectively.
ePasslet Suite website: https://www.cryptovision.com/en/products/security-token-hardware-solutions/epasslet-suite/

by Klaus Schmeh | Feb 3, 2025 | Newsticker, Product & Solutions
Eviden Digital Identity has enhanced cryptovision SCinterface VSC, the extension to the middleware SCinterface, by expanding support to Linux, significantly broadening its capabilities beyond the previously supported Windows environment. SCinterface VSC enables users to utilize Trusted Platform Modules (TPM) as virtual smart cards, overcoming the constraints of traditional physical smart cards.
Building on the discontinued Microsoft VSC, SCinterface VSC delivers improved compatibility and flexibility, offering organizations a seamless experience across platforms. With this expansion, Linux users can now access the same secure authentication and cryptographic functionality once exclusive to Windows, creating a unified virtual token experience.
With SCinterface supporting over 100 different profile cards and platforms, SCinterface VSC ensures a smooth transition for organizations looking to modernize their digital identity management. Notably, it allows the concurrent use of both physical tokens and virtual smart cards, providing users with versatile options for secure access.
Key benefits of SCinterface VSC include:
- Easy migration from physical tokens to virtual formats.
- Broad operating system support
- Future-proof key material compatibility
SCinterface VSC website: https://www.cryptovision.com/en/products/credential-management/cryptovision-scinterface-vsc/

by Klaus Schmeh | Dec 16, 2024 | Newsticker, reference
Eviden, the Atos Group business leading in digital, cloud, big data and security announces today that it has been awarded the national C-ITS PKI contract by France’s Department for Transport Infrastructure and Mobility Services (DGITM). Under this four-year contract, which includes two optional years extensions, Eviden will deploy its IDnomic C-ITS PKI solution to support secure and interoperable communication across all C-ITS in France. The nationwide deployment is slated for 2025.
France, one of the leading countries in C-ITS, has chosen to acquire its own national C-ITS PKI in accordance with the European technical and security policy frameworks. Eviden’s IDnomic C-ITS PKI will be crucial to ensure the security and privacy of this system.
Simon Ulmer, Group VP, Head of Digital ID at Eviden, Atos Group: “This selection by the French government to supply and operate the new national ‘PKI C-ITS FR’ further demonstrates Eviden’s leadership in C-ITS security. This collaboration underscores the excellence of our solutions. We are honored by the ministry’s trust and excited to continue advancing the French C-ITS ecosystem towards safer, smarter, and greener mobility.”
IDnomic C-ITS PKI website: https://www.cryptovision.com/en/products/pki-solutions/idnomic-c-its-pki/

by Klaus Schmeh | Dec 10, 2024 | Company, Newsticker
Markus Hoffmeister, founder and long-standing managing director of cv cryptovision GmbH, and Marco Smeja, sales manager and also long-standing managing director, will be leaving the company at the end of the year to pursue new personal and professional goals. With visionary leadership, tireless commitment and outstanding contributions, both have played a decisive role in shaping cv cryptovision GmbH. The development of the company into an international player and the impressive sales growth of the last 25 years are among the most important milestones of their successful work.
Continuity and a breath of fresh air
Thomas Riechmann, part of the management team since 2021, remains on board as an experienced constant and will continue to represent the values and visions of cv cryptovision GmbH.
Two familiar faces from the company’s own ranks are also joining the management team:
- Björn Burzynski (previously COO and CFO): Since joining the company in 2020, he has contributed significantly to the optimization of internal structures and sustainable growth with extensive expertise in finance, organization and corporate management.
- Kerstin Honskamp (previously Head of Product Management): Since 2020, she has been strengthening the product portfolio with her experience in product strategy and innovation management and driving forward pioneering developments.
This combination of consistency and new impetus ensures that cv cryptovision GmbH will remain a reliable partner for innovative solutions in the future.

Björn Burzynski and Kerstin Honskamp (left) replace Marco Smeja and Markus Hoffmeister (right) on the management board. Thomas Riechmann (center) remains on board as an experienced constant.
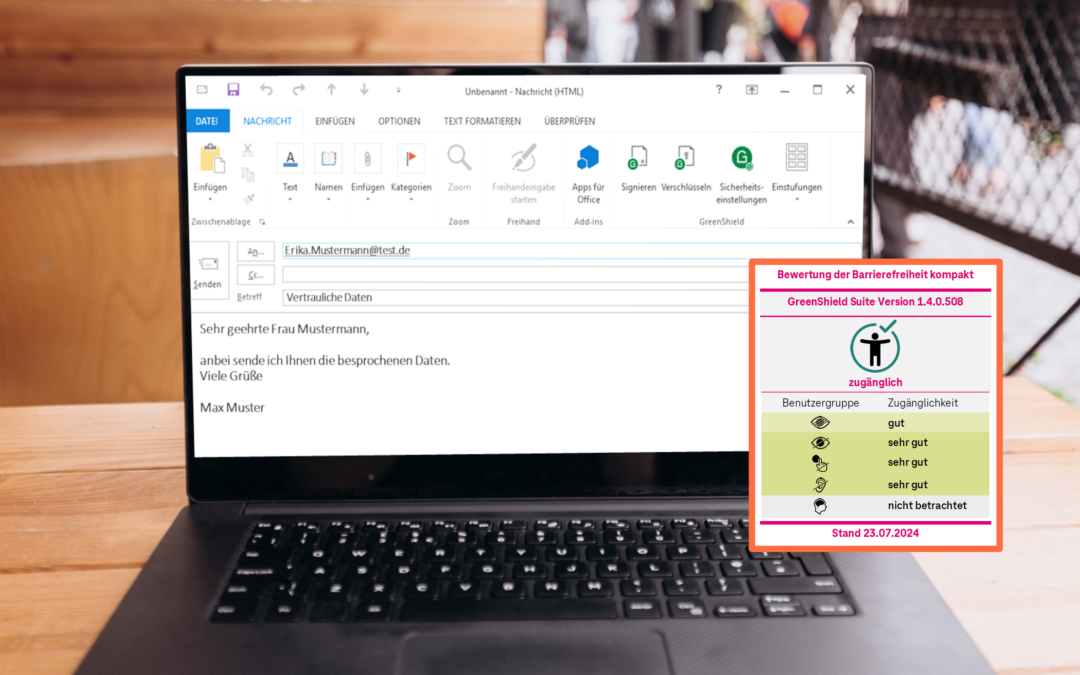
by Klaus Schmeh | Dec 6, 2024 | Product & Solutions
The GreenShield Mail and GreenShield File encryption software sets new standards in terms of accessibility. The DAkkS-accredited test report for version 1.4.0.508 of the GreenShield Suite confirms excellent results: The software is easily accessible for users with impaired vision or without color perception and proves to be particularly user-friendly for people without vision as well as for users with motor or auditory impairments. GreenShield thus offers an accessible solution that stands out in its category and is fully suitable for different user groups.
Deutsche Telekom confirms: “cryptovision impressed us with the test report on the accessibility of the GreenShield software. In addition, cryptovision is the first manufacturer I know of to deliver the test report directly with the software. That is remarkable.”
GreenShield website: https://www.cryptovision.com/en/products/security-applications/greenshield/

 CLOUD SERVICES
CLOUD SERVICES CITIZEN ID
CITIZEN ID IT SECURITY
IT SECURITY IOT and INDUSTRY
IOT and INDUSTRY PKI SOLUTIONS
PKI SOLUTIONS CREDENTIAL MANAGEMENT
CREDENTIAL MANAGEMENT SECURITY TOKEN & HARDWARE SOLUTIONS
SECURITY TOKEN & HARDWARE SOLUTIONS SECURITY APPLICATIONS
SECURITY APPLICATIONS



