Interesting facts from the field of encryption

Source: Schmeh
Did you know that the history of cryptography can be divided into three eras? In the first era, which began in ancient times, encryption was still done by hand – for example, with paper and pencil or with mechanical disks. In the second era, which lasted from about 1920 to 1970, special machines were used for ciphering. In the third era, computers took over this task.
Other Source: Wikipedia article on the history of cryptography

Source: Pixabay
As early as 3,500 years ago, people used cryptography to protect sensitive information. The oldest known example comes from Mesopotamia: Around 1,500 B.C., a potter there encrypted the recipe for a ceramic glaze written on a clay tablet. Presumably, he wanted to prevent his competitors from reading it. So industrial espionage must have been a problem even back then.
Other Source: David Kahn: The Codebreakers. Scribner, 1996

The oldest known tool used for encryption is the scytale. This consists of a round wooden stick, around which a tape is wound. On this one notes (along the rod) the message and unwinds it again. Only the ribbon is sent to the recipient. The recipient can decrypt the message only with the help of an identical scytale (i.e. with a stick of the same diameter). The scytale was already known to the ancient Greeks. Whether they actually used it, as the historian Plutarch reports, is disputed among historians.
Other Source: Thomas Kelly: The Myth of the Skytale. Cryptologia 3/1998
The Caesar cipher

Source: Pixabay
The encryption methods known in ancient times were not yet particularly secure. This also applies to the “Caesar cipher”. With this method, all letters of the alphabet are shifted by a fixed value, for example by four digits. Thus, the plaintext word POST becomes the encrypted word SRVW. The term “Caesar cipher” goes back to the Roman general Gaius Julius Caesar, who, according to the Roman writer Suetonius, used this type of secret communication for his military correspondence. In doing so, Caesar is said to have shifted the alphabet by three letters.
Other Source: Elonka Dunin, Klaus Schmeh: Codebreaking: A Practical Guide. Robinson, 2020

Source: Wikimedia Commons
All in all, the cryptographic achievements of the Greeks, Romans, and Babylonians seem quite modest compared to what the scholars of the time accomplished in other disciplines – such as astronomy or mathematics. Cryptography first blossomed in Arabia in the late first millennium. An important crypto pioneer was the polymath Al-Kindi, who around the year 800 wrote, among other things, the first known treatise on solving encryptions. Al-Kindi recognized in particular that the frequencies of letters are extremely helpful here. It was not until the 15th century that such findings also became established in Europe.
Other Source: Tariq Al-Tayeb: Al-Kindi, Cryptography, Code Breaking and Ciphers, 2003

Source: Beinecke Library
Probably the most famous (presumably) encrypted document in the world is a 230-page book from the 15th century: the Voynich Manuscript. This is written in a script that no one can read. The numerous illustrations show, among other things, plants that cannot be identified, as well as rosettes whose meaning also poses a mystery. Despite numerous attempts, it has not yet been possible to decipher the Voynich Manuscript. Linguistic studies suggest that it is not a simple encryption of an ordinary text. It is quite possible that the contents of the book have no meaning at all.
Other Source: Websites of René Zandbergen, Nick Pelling and Richard SantaColoma
Source: Gerald Rottstedt
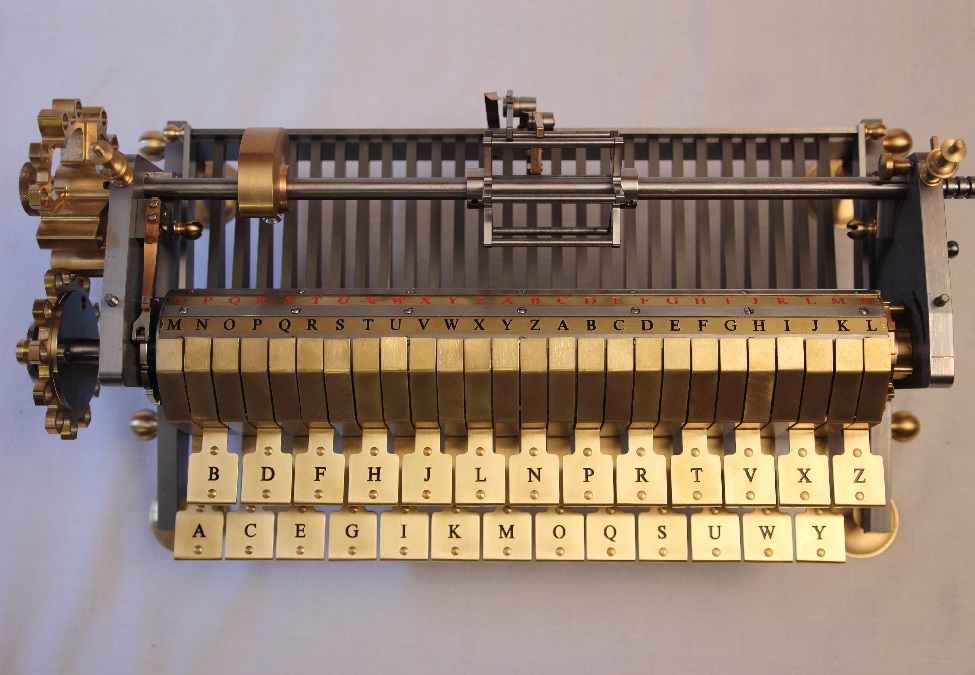
The German scholar Gottfried Wilhelm Leibniz (1646-1716) was not only a philosopher, jurist, historian and political advisor, but also described an encryption machine as early as the 17th century. He presented this “Machina Deciphratoria” to Emperor Leopold I in Vienna in 1688. But Leopold refused, because his advisors (wrongly) considered the encryption methods used at the time to be secure. With his invention, Leibniz was a good 200 years ahead of technical developments. Since 2014, there has been a replica of the Machina Deciphratoria, which existed only in the form of drawings in Leibniz’s day.
Other Source: Ralf Bülow: Herr Leibniz und seine Chiffriermaschine

Source: National Cryptologic Museum
The US politician Thomas Jefferson (1743-1826) also invented an encryption method: the Jefferson disk. Such a device consisted of 36 rings of letters mounted on an axle. On these, the user set the plaintext and then read the ciphertext. The security of the encryption that could be realized in this way was remarkable. Jefferson was also far ahead of his time: it was not until around 1920 that the U.S. military used a comparable device on a larger scale for the first time. As late as World War II, cipher disks were still being used for less important messages.
Other Source: Wikipedia article about the Jefferson disk

Source: Wikimedia Commons
The Enigma was the Germans’ most important encryption machine during World War II. About 30,000 copies were built and used primarily to encrypt Morse code messages. Even before World War II, however, Polish mathematicians succeeded in cracking the Enigma. Later, the British were able to continue this work and decipher hundreds of thousands of intercepted Enigma messages at their “deciphering factory” in Bletchley Park. Thousands of workers and state-of-the-art data processing technology made this possible. These deciphering successes proved to be an enormous advantage for the British in the war against the Germans. Today, original Enigmas are coveted collectibles for which six-figure sums are paid.
Other Source: Wikipedia article on the Enigma
World War II

Source: Schmeh
In addition to the Enigma, the Germans used several other encryption machines during World War II. These included the following:
- Lorenz machine (SZ-40/42): Used at the highest military levels, this teletype key machine was cracked by the British using the computer precursor “Colossus”.
- Siemens & Halske T52 (Geheimschreiber): This teletype key machine, also used for important messages, was solved in an early version by the Swedish mathematician Arne Beurling.
- Siemens & Halske T43: The T43 implemented a one-time pad and was thus in theory unbreakable.
- Key Device 41 (Hitler Mill): The Hitler Mill was a German development of a Hagelin machine. It was intended to replace the Enigma, but was not used on a large scale.
- Kryha Standard: This device from the 1920s was not particularly secure. The German secret service in South America used it nevertheless.
- Hellschreiber: An encryption device made by the Kiel-based company Rudolf Hell. Little is known about this machine.
Other Source: A complete (?) list of German cipher machines in World War 2

Source: Wikimedia Commons
At the end of the sixties, a serial killer was on the loose in the San Francisco area: the Zodiac Killer. In addition to his crimes, he sent a total of four encrypted messages to the public. One of them was solved in 1969, another one in 2020, but these deciphering successes could not contribute to the identification of the killer. The two remaining messages from the Zodiac Killer remain unsolved to this day. The perpetrator has never been caught.
Other Source: David Oranchak‘s Website
Data Encryption Standard (DES)
Source: Wikimedia Commons
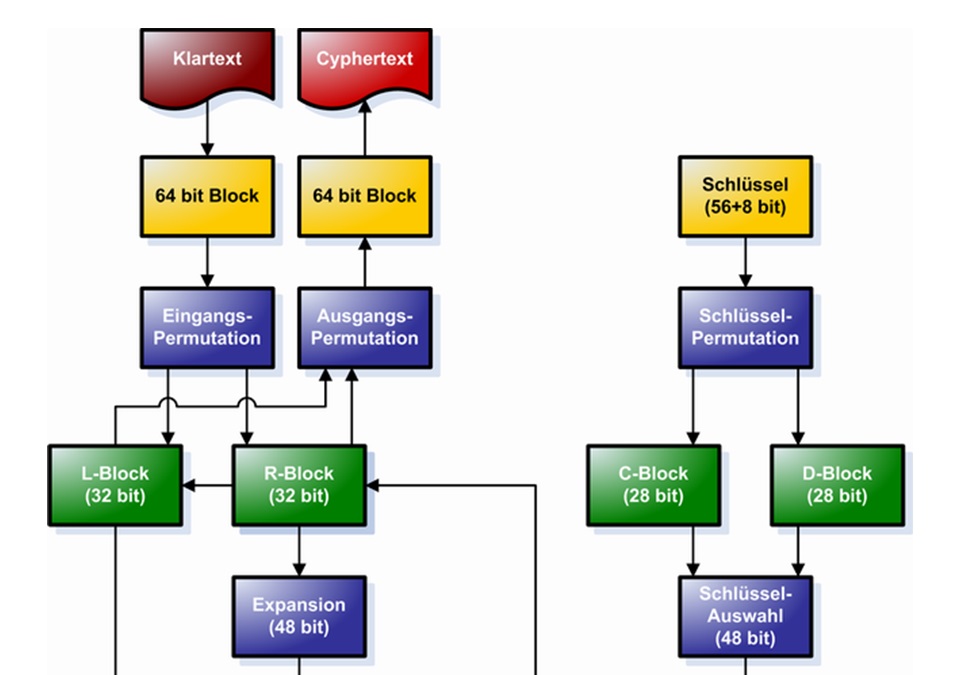
When the computer came along around 1970, completely new encryption methods were needed that took digital technology into account. The then market-leading computer company IBM developed such a method. It was standardized as the Data Encryption Standard (DES) in 1976 after a number of changes. The DES quickly gained acceptance and was used in ATMs, encryption programs, online banking solutions, radios, locking systems and pay TV, among other applications. The DES also served as a model for numerous other encryption algorithms that have emerged in recent decades. Even today, the DES – especially the triple DES variant – is used in many computer systems.
Other Source: Klaus Schmeh: Kryptografie – Verfahren, Protokolle, Infrastrukturen. Dpunkt 2016

Source: cryptovision
For centuries, users of cryptography had to struggle with a problem: in order to encrypt securely, it was necessary to agree on a key beforehand (key exchange problem). It was not until the 1970s that a practical solution was finally found: asymmetric cryptography. This involves using a different key for encryption than for decryption. Since the former can be made public, there is no need to agree on a key by secret means. Among the pioneers of asymmetric cryptography were the Americans Whitfield Diffie and Martin Hellman with the Diffie-Hellman key exchange named after them, which is still widely used today. The RSA method named after Rivest, Shamir and Adleman, which emerged a short time later, became even more popular. Today, it is impossible to imagine the Internet without asymmetric cryptography. From web browsers to home office solutions to e-mail clients, hardly any online application can do without RSA or Diffie-Hellman.
Other Source: Klaus Schmeh: Kryptografie – Verfahren, Protokolle, Infrastrukturen. Dpunkt 2016
Source: cryptovision
In the late nineties, a new family of asymmetric crypto methods emerged: Methods based on elliptic curves. These worked much faster and with shorter keys than RSA or Diffie-Hellman, for example. Computer expert Markus Hoffmeister from Gelsenkirchen recognized the advantages of this technology and founded cryptovision together with his brother Andreas in 1999. The goal of the two young entrepreneurs was to bring procedures based on elliptic curves to the market in practical products. Today, cryptovision has 70 employees.
Other Source: Klaus Schmeh, Thomas Zeggel: Standardsuche. iX 5/2015, Seite 94
Post-quantum cryptography
Source: cryptovision
Currently, a new generation of asymmetric crypto methods is emerging: those that are not vulnerable to quantum computers (post-quantum methods). Quantum computers use the principles of quantum mechanics and can hardly be compared to conventional computers. They can crack asymmetric encryption methods such as RSA, Diffie-Hellman or elliptic curve methods in a short time. Quantum computing technology is still in its infancy and therefore does not pose a threat yet. However, this could change, and therefore it is already worthwhile to look into post-quantum methods. This is anything but easy, because these methods are mathematically demanding and diverse. cryptovision has set itself the goal of explaining post-quantum methods in an understandable way – for example, with comics that are incorporated into articles and conference presentations. Even at the renowned RSA conference in San Francisco, cryptovision was already present with such a presentation.
Other Source: cryptovision whitepaper: Vertrauliche Daten auch für die Zukunft schützen
Source: Klaus Schmeh: Codeknacker gegen Codemacher. W3L, 2014
 CLOUD SERVICES
CLOUD SERVICES CITIZEN ID
CITIZEN ID IT SECURITY
IT SECURITY IOT and INDUSTRY
IOT and INDUSTRY PKI SOLUTIONS
PKI SOLUTIONS CREDENTIAL MANAGEMENT
CREDENTIAL MANAGEMENT SECURITY TOKEN & HARDWARE SOLUTIONS
SECURITY TOKEN & HARDWARE SOLUTIONS SECURITY APPLICATIONS
SECURITY APPLICATIONS